Recap: GoDaddy Bug - Certificates issued without proper domain validation
In late December 2016 I found a bug regarding GoDaddy’s domain validation, I was using Microsoft’s Azure portal as usually and created some certificates for domains. I noticed that some were issued with valid certificates for domains that did not even point to a valid server.
After doing some testing I found that the validation process was broken:
Specify a local address (127.0.0.1) as an A record in the domain dns settings, and you will get a valid certificate
However, after reporting the issue it turns out there is a more: Invalid validation also occurs on an misconfigured web server, that echos GoDaddy’s validation token.
GoDaddy’s validation process looks like this (simplified):
- Generate a token and ask the owner to put this token in a textfile (or similar) on their webroot
- GoDaddy looks if the token is in that file
- If the token was found the valdiation is successful
However if you set up a server that simply echos all data it gets. Such as the Apache Error page…
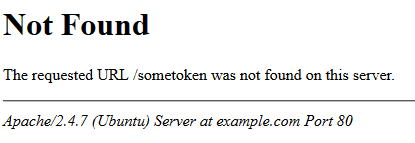
… the token will be printed and the validation succeeds.
Thats why thousands of certificates have been issued without a propper validation.
Report
I thought (at this time) that Microsoft validates the owner/server and just pulls the certificates directly from GoDaddy. I was not aware that Microsoft is just a reseller. Thats why I reported the bug to Microsoft initially.
Some time passed and Microsofts response was something like “it is not a bug”.
OK, well then I explain some scenarios. MITM attacks, identity theft,…
Time passes and passes…
They responded and and told me they forwarded the issue to GoDaddy, GoDaddy will contact me. So far so good.
Long story short: GoDaddy never contacted me.
By browsing HN, I found out that the issue was allready fixed.
Some more time passed (3 months later) and I signed up on Cobalt and requested an invite to GoDaddy’s program, explaining that I reported the issue a while back.
I explained the Issue in detail again. And recived a bounty.
Timeline
| 19 Dec 2016 | Reported Issue to Microsofts security team |
| 27 Dec 2016 | Recived first response |
| 3 Jan 2017 | MSRC Case opened |
| 11 Jan 2017 | GoDaddy fixes bug, Wayne Tyer (CEO of GoDaddy) explains issue on moz.dev.security.policy |
| 17 Jan 2017 | Asked GoDaddy HQ for the status -> No response |
| 10 Mar 2017 | GoDaddy adds me to Cobalt program |
| 12 Mar 2017 | Explained issue to GoDaddy over Cobalt |
| 17 Apr 2017 | Recived $3000 bounty |